DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
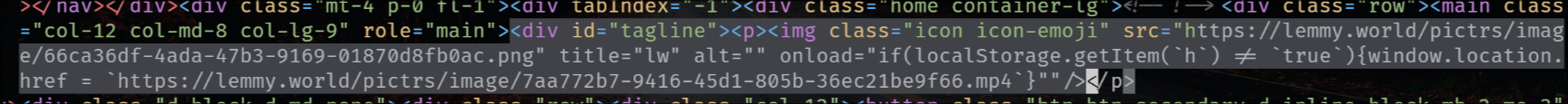
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


So any comment or post?
Yes, so you don’t even need to compromise an admin account
So maybe the admin account was compromised as a result of the hack, rather than the other way around?
the hacker could use a cookie stealer injected by the xss to steal the admin account.
I think that’s right on the money.
https://lemmy.sdf.org/comment/850269
That makes more sense.